Protect Your Business from Login Credential Hacks in 2025
Hackers are no longer breaking in—they’re gaining access by using your login credentials.
With the ever-changing landscape of technology, hackers are also changing how they execute attacks. They no longer break down the door—they’re sneaking in with a stolen key instead: your login credentials.
Identity-based attacks are quickly becoming the top way for hackers to get into systems. They steal passwords, fool employees with legitimate-looking (but fake) emails, and overload people with login requests until someone slips. Unfortunately, it’s working.
In 2024, one cybersecurity firm found that 67% of major security breaches stemmed from stolen login credentials. Even giants like MGM and Caesars fell victim to these types of attacks last year—proving that no business, big or small, is immune.
 Here’s how they’re getting in:
Here’s how they’re getting in:
Stolen passwords are the simple start. But hackers are getting more sophisticated with their attacks:
-
Fake emails and login pages trick employees into inputting their information.
-
Hackers are stealing text messages for 2FA (two-factor authentication) codes by SIM swapping.
-
Fatigue attacks flood your phone with Multi-Factor Authentication (MFA) requests until you accidentally hit “approve.”
Employee personal devices and outside vendors like your help desk and call centers aren’t safe either!
How to protect your business login credentials:
The great news? You don’t need to be a tech genius to safeguard your business. Small, smart steps are all it takes.
1. Ditch 2FA and transition to MFA:
The days of using text messages to verify your identity are long gone. It’s time to step up your tech game just like hackers have stepped up theirs. Using app- or security-based Multi-Factor Authentication is far safer than text messages (remember, criminals can SIM swap and get those texts). Apps like Microsoft Authenticator, Google Authenticator, DUO Mobile, and physical keys like the UbiKey are the future of cybersecurity.
2. Train your team:
The best way to prevent being hacked is to know what a scam looks like. Your security is only as strong as your weakest link. If your dental assistant can barely operate their email inbox, they’re certainly not going to recognize a scam. Teach your employees to spot fake emails and suspicious requests—and what to do when they receive one. We offer FREE Cyber Security Training to ALL business owners in our communities. Click HERE to sign up!
3. Limit Access:
If employees don’t need access for their daily functions, don’t give it to them. This safety net just makes sense: even if a hacker gets into your assistant’s computer or email, limited access means they won’t get far.
4. Use Strong Passwords For Login Credentials:
We know—you’ve probably heard this a thousand times. But you wouldn’t believe how often we help someone whose password is… found wanting. We professionally recommend passwords be at least 16 characters long, with a mix of lower- and uppercase letters and special characters. Yes, that’s a lot to remember—especially when you’re using unique passwords (as you should be doing, cough cough).
5. Use a computer-based password manager:
As mentioned, your passwords should be long, complex, and unique for every login. If you have 38 places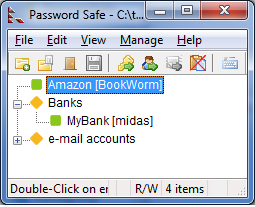 to log in, that’s an impossible number of passwords to remember. We suggest using a password manager to store your passwords—but not an online one like Google. Download a computer application-based program such as KeePass or PWSafe to store your passwords locally. Then you only have one complex password to remember.
to log in, that’s an impossible number of passwords to remember. We suggest using a password manager to store your passwords—but not an online one like Google. Download a computer application-based program such as KeePass or PWSafe to store your passwords locally. Then you only have one complex password to remember.
The bottom line:
Your login credentials are precious gems that cyber criminals are scouring the world wide web for like digital pirates in search of buried treasure—and they’re getting more ingenious and intuitive (ingenuitive, if you will) every day.
Staying ahead of them might sound daunting—but it doesn’t have to be. That’s where we come in. Think of us as your cybersecurity compass: helping you chart a safer course, avoid digital traps, and protect your business without making things harder for your team.
Want to know if your business is vulnerable? Let’s talk. We’d love to set up a discovery call to discuss your business’s unique security needs, click here to schedule at your convenience. If you need immediate assistance, don’t hesitate to call us directly at 541-494-2099.
